As more and more connected devices are released, the number of attack vectors available to hackers and malicious parties increases. Not even DSLR cameras, seemingly benign and secure devices, are safe; in a demonstration by security experts at Check Point Research shows, DSLRs can be quite susceptible to ransomware, even from a distance.
The attack demonstrated by Check Point Research exploits a relatively new feature of DSLRs: WiFi connectivity. Most modern DSLRs can use a file transfer protocol called Picture Transfer Protocol (PTP) to send photos from the camera straight to a connected computer. Newer DSLRs, like Canon’s EOS 80D, also include WiFi cards that enable the camera to use PTP/IP, or PTP over a wireless connection.
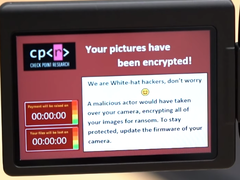
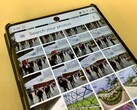
Apparently, PTP/IP isn’t terribly secure. Using a custom Python script, the researchers were able to sniff out the camera’s network connection and hijack it to load ransomware onto the camera’s SD card. This ransomware then auto-executed and encrypted the user’s photos. As a last touch, the ransomware loaded a WannaCry-like image stating that the photos had been encrypted. All this was done in close proximity to the camera, but no physical connection was required.
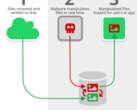
The researchers said that the vulnerabilities present in Canon’s implementation of PTP and PTP/IP make Canon DSLRs a unique and tempting target for attackers. If an attacker could load access both the camera and the user’s computer (which could be done when the user connects their camera or inserts their infected SD card), malware could be loaded to fully encrypt the user’s photos, delete images, or more. Malicious parties could even use a camera as a launching point. Infecting a photographer’s SD card with malware may prompt them to insert the card into their computer to check for issues, which could then open the user’s entire computer to attack.
Check Point Research notified Canon of these vulnerabilities in March, and Canon pushed out a security patch on August 6th. If you own a Canon DSLR, it may be a good idea to download and install the latest firmware.