It seems that there’s always a new piece of malware wreaking havoc in the Android world. Oftentimes, a quick virus scan or factory reset will delete the malicious app and eliminate the threat. However, there is a relatively new trojan that has been able to evade most antivirus measures and reinstall itself, even after a factory reset.
The xHelper trojan, which was discovered in early 2019. The trojan is a rudimentary piece of malware that mainly uses the infected device’s resources to visit ad pages in order to generate revenue. This, in turn, hogs system resources and can rack up data usage, a particularly poignant problem for those on restricted or metered connections.
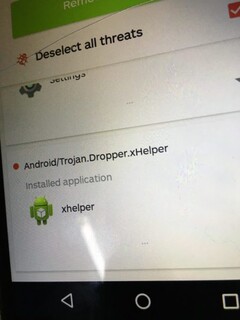
The biggest problem with xHelper is the sneaky way in which it persists. Upon installation, the trojan buries a dropper deep in the Android file system that is largely ignored by antivirus checks. Even worse, the dropper persists even after a factory reset. The dropper will then reinstall the trojan and drop more malware before uninstalling itself to remain hidden.
While the exact mechanics of how xHelper works are still not fully known, Malwarebytes has devised a plan of action to permanently remove the trojan. If you suspect your device of being infected by xHelper, run a virus scan with any reputable antivirus software. If xHelper pops up, Malwarebytes suggests you follow these steps (from the Malwarebytes blog). Note: these steps were devised with the help of a Malwarebytes forum user by the name of Amelia.
- We strongly recommend installing Malwarebytes for Android (free).
- Install a file manager from Google PLAY that has the capability to search files and directories.
- Amelia used File Manager by ASTRO.
- Disable Google PLAY temporarily to stop re-infection.
- Go to Settings > Apps > Google Play Store
- Press Disable button
- Run a scan in Malwarebytes for Android to remove xHelper and other malware.
- Manually uninstalling can be difficult, but the names to look for in Apps info are fireway, xhelper, and Settings (only if two settings apps are displayed).
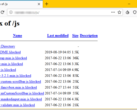
- Open the file manager and search for anything in storage starting with com.mufc.
- If found, make a note of the last modified date.
- Pro tip: Sort by date in file manager
- In File Manager by ASTRO, you can sort by date under View Settings
- Delete anything starting with com.mufc. and anything with same date (except core directories like Download):
- Re-enable Google PLAY
- Go to Settings > Apps > Google Play Store
- Press Enable button
- If the infection still persists, reach out to us via Malwarebytes Support.