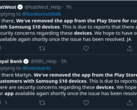
Linux is known for two things in the computing world: its open-source constructions and its security. Since Linux is built differently than Windows, it is typically much harder to infect a Linux-based system with malware or ransomware. Even still, there’s a new breed of ransomware that is infecting an increasing amount of Linux servers. The Lilu (or Lilocked) ransomware now affects thousands of Linux servers worldwide.
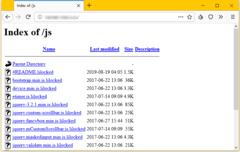
There is not a lot known about the ransomware or how it works, but it seems to be specifically targeting Linux servers. Lilu will infect a server and locked specific files by changing their file type with a “.lilocked” extension. The attack also leaves a note that states:
I’VE ENCRYPTED ALL YOUR SENSITIVE DATA!!! IT’S A STRONG ENCRYPTION, SO DON’T BE NAIVE TO RESTORE IT;) [SIC]
YOU CAN BUY A DECRYPTION KEY FOR A SMALL AMOUNT OF BITCOINS!
YOU HAVE 7 DAYS TO DECRYPT YOUR FILES OR YOUR DATA WILL BE PERMANENTLY LOST!!!
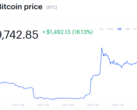
The note includes an Onion site in which users can paste a key provided at the end of the note. After entering the key, users will be prompted to deposit either 0.03 BTC (~US $310.83 as of publication) or US $325 into an Electrum wallet. After the money is deposited, all of the user’s affected files will then be decrypted, also this has not been verified and relies fully on the promise of the malicious party.
The good news for affected users that, unlike similar attacks such as WannaCry, system files are left unaltered. Instead, Lilu seems to be targeting HTML, JS, CSS, PHP, and image files. While the attack is likely to derail development or media projects, it doesn’t seem to be affecting the Linux servers as a whole. To date, affected Linux systems are still able to operate normally.
Current estimates peg the number of affected systems at about 6700. This estimate may be too low as many infected servers that have reported the malware are not indexed by Google or other search engines (i.e., deep and dark web servers).
The exact mechanics of Lilu are still unknown, so there is currently no method to prevent or protect against the ransomware outside of user competency and awareness. As always, avoid opening suspicious or unknown links and files, and only download applications and dependencies from official repositories.