Cyber attacks are on the rise, and security researchers at the Microsoft Threat Intelligence Center have discovered a new intrusion method through an increasingly popular avenue: connected devices, or the Internet of Things.
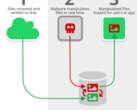
Researchers at Microsoft discovered a new attack line, attributed to Russian cyber espionage group STRONTIUM (aka Fancy Bear, APT28, Pawn Storm, and other aliases), that exploits the lax control of internet-connected devices. While device specifics weren’t given in their report, the researchers stated that “popular IoT devices” including a Voice-over-Internet-Protocol (VOIP) phone, a printer, and a video decoder were targeted by attackers to gain access to connected network infrastructure.
In the attack, the hackers gained access to the IoT devices and used shell scripts to sniff network traffic for connections to local subnets, opening other devices on the same network to attack. The attackers also used a relatively simple script to “establish persistence on the network,” enabling them to retain access for an indefinite period of time.
While Microsoft did not comment on the extent or impact of the attack, the research team pointed out that initial access was possible because of poor device management on the victim’s part. Specifically, the default password for two of the devices (set by the manufacturer) had not been changed. The third device was running older software and had not had the latest security update installed.
The research team concluded that as IoT devices are becoming more popular in the enterprise sector, the vulnerabilities in these devices can open organizations up to attack through unexpected vectors. According to Microsoft, the “number of deployed IoT devices outnumber the population of personal computers and mobile phones combined.” As technology progresses, so too do the methods and avenues of cyberattacks.
The research team concluded their study with several suggestions for securing IoT devices, including employing stricter controls on IoT devices that are connected to corporate networks, running a separate and isolated network for IoT devices, and consistent monitoring of IoT devices to detect any odd behavior such as pings to external servers. A full list of recommendations can be found on the Microsoft Research Center blog.