Over the past weekend, a cybersecurity researcher discovered a widespread attack that exploits a vulnerability in older Windows systems. The attacker was able to remotely install a cryptocurrency miner, though the damage could have been much worse.
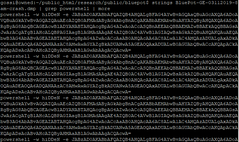
Kevin Beaumont, a security researcher, discovered the attack after setting up a handful of systems running older versions of Windows. The attack exploited a vulnerability dubbed BlueKeep that takes advantage of a flaw in the Remote Desktop Service feature of older systems.
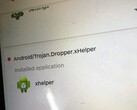
Working with MalwareTech (Marcus Hutchins), the researcher that found the WannaCry killswitch, Beaumont discovered the worm could invisibly infect vulnerable machines and install a Monero Miner, all without the knowledge of the end-user.
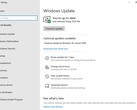
Microsoft announced the vulnerability and released a patch this past May. The company pushed users to install the patch again over the summer. The flaw is so widespread that even the NSA has urged users to update their machines.
Why is this important? BlueKeep affects machines running Windows 7, Windows Vista, Windows XP, Windows Server 2003, and Windows Server 2008 that have the Remote Desktop Service activated. While most individual PC users likely own a machine running Windows 10, several businesses, hospitals, and government agencies still run older versions of Windows. If these organizations haven’t updated their systems with the latest patch, which is likely, their computers may be ticking timebombs.
The security patch for BlueKeep can be found on Microsoft’s website here.