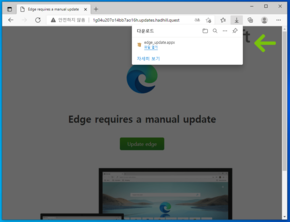
Magniber is a ransomware that is being distributed using vulnerabilities known in Internet Explorer for quite some time now. However, analysts at the South Korea-based AhnLab Security Emergency Response Center (ASEC) have now discovered that Magniber is also being distributed via Microsoft Edge and Google Chrome disguised as a legitimate update package.
The Magniber ransomware infects vulnerable PCs running Edge and Chrome in the form of a browser update package. The malware is distributed as a signed .appx update package with a valid certificate. This means that Windows assumes this is a valid app and proceeds with installation. Once installed, the malicious .appx package creates two files — wjoiyyxzllm.dll and wjoiyyxzllm.exe — in a non-descript path within C:\Progam Files\WindowsApps. As most users will know, this is actually a protected folder meant only to contain properly signed Microsoft Store apps.
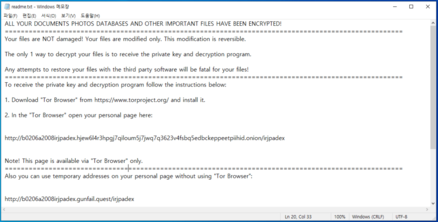
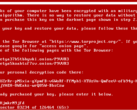
wjoiyyxzllm.exe loads wjoiyyxzllm.dll and executes a strange function called "mbenooj". The DLL file downloads the ransomware payload and decodes it. After this, the Magniber ransomware gets executed from memory of wjoiyyxzllm.exe and encrypts the user's files. A ransom note is then shown demanding money transfer in order to decrypt the data.
Though Magniber is not known to steal any files, it is currently not possible to decrypt and restore functionality without paying the ransom (this is assuming that the decryption key is even provided upon payment in the first place).
Therefore, it goes without saying that users should be careful while downloading files from various sources. Even signed .appx files can be potentially dangerous when obtained from unverified sources. Ensure that your critical data is always backed up and your security software's definitions are up to date.
You can also use Windows Defender's Controlled Folder Access function to prevent unauthorized access to critical files. For more information, check out our tutorial on how to enable Controlled Folder Access in Windows 10.