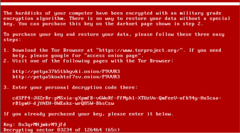
The original Petya ransomware inflicted damage on quite a number of PCs and posed a huge security concern. The developer behind the original Petya ransomware, Janus Cybercrime Solutions, has now made available the decryption key required to decrypt the files that the ransomware encrypted. Though late in arrival, the decryption key, the link to which was made available on Twitter by the developer, has been found to be effective only against the three variants of Petya that exist. Security researchers tried to use the key against the much more destructive NotPetya but met with little success.
Petya, originally was not intended to take the entire PC for hostage, save a few files. NotPetya, however, is much more destructive in its approach and locks down the whole PC as it first attacks the Master Boot Record (MBR) that Windows uses for booting up and then starts encrypting all files on the drive. NotPetya exploited the EternalBlue loophole that was also used by the earlier WannaCry ransomware. Microsoft had patched EternalBlue much prior to the NotPetya outbreak.
With the Petya attack happening sometime in 2016, most victims either coughed up money for decryption, or have gone ahead and formatted their storage. Victims of NotPetya had a glimmer of hope that the Petya decryption key would work for them as well but, unfortunately, the Petya key does not seem to affect NotPetya infected PCs in any way. Even the Bitcoin account to which NotPetya demanded the ransom to be sent has stopped working. With enterprises and end-users actively patching their PCs, NotPetya was stopped in its tracks, but PCs that are already infected have no known cure in sight. It is therefore advised that users follow safe practices online and keep their systems up-to-date with the latest security updates.