A relatively new piece of ransomware, called Cicada3301, has been analyzed in detail by cybersecurity researchers, and the findings reveal surprising callbacks to infamous attacks from the recent past. Cicada3301 is able to target Linux-based and Windows systems.
This new malware bears a resemblance to BlackCat, the ransomware used in the 2021 attack on the Colonial Pipeline. The unique factor is that Cicada3301 uses a two-pronged approach to make victims pay up; not only are files encrypted, they're also packaged and leaked if payment isn't made.
Cicada3301 was first spotted in June of 2024, when the first leak of a victim's data showed up on the dedicated site set up by its creators. They later took to a Russian dark web forum called RAMP with the aim of soliciting affiliates. They offered Cicada3301 as a service, offering to attack selected targets for a price. This model, called ransomware-as-a-service, has gained popularity among bad actors in recent years.
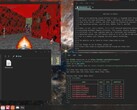
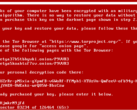
Victims will find their systems largely immune to traditional efforts used to stem ransomware attacks thanks to a clever mix of tactics built into Cicada3301. They will instead be greeted by a lone text file offering instructions to save their files from being leaked. According to the text file, the group behind this attack includes an offer to tighten up victims' security to prevent similar attacks in the future, as well as ongoing support, should a victim choose to pay up.
The website and resources utilized by the group behind the 2021 attack were eventually seized by US authorities. It is believed that the group has ceased activities, but the similarities that Cicada3301 bears to BlackCat and its rebrand, ALHPV, are numerous.
Cicada3301 is written in the Rust programming language, making it versatile, efficient, and extensible, but this could be written off as merely following the trend established by BlackCat; up until that attack, ransomware written in Rust was extremely uncommon, and was more often than not a mere proof-of-concept shown off by white hat hackers across the web.
Beyond using the same programming language and general attack structure, Cicada3301 uses similar decryption methods, and many commands written into the new malware are exactly the same as function calls found in BlackCat. In both attacks, legitimate user credentials are obtained through any available means, often social engineering, and used to gain access to the target system.
From there, both attacks use almost identical calls to do things like phone home, encrypt and decrypt files, display messages, and more. Cicada3301 does, however, come with some new tricks. Chief among them is the ability to stop outside machines, including virtual machines, from accessing encrypted files and systems.
As of September of 2024, all resources linked to Cicada3301 are seemingly still live, and there have been no reports of any bad actors connected to it stepping down or being apprehended. It is possible that the new ransomware is the creation of one or more team members from the BlackCat attacks, or a rival group that copied much of the code of BlackCat before it went dark.