Back in March, Wikileaks exposed CIA’s digital surveillance plans by releasing important information regarding the Vault 7 project. It immediately became clear that the intelligence agency ‘hoarded’ vulnerabilities, which, in turn, have been hacked away from CIA and could be used to attack unprotected systems all across the world at any given time. Unleashed in April, the WannaCrypt ransomware supposedly used zero-day vulnerabilities stolen from CIA. Microsoft was able to release an update that addressed such vulnerabilities prior to the release of the infamous ransomware.
The latest ransomware worldwide attack occurred a week ago and once again stirred up controversies involving the security of Windows 10. Microsoft inspected all possible disrupting agents and now has released a full analysis of the Petya attack. Microsoft confirms that Windows 10 was already protected against Petya, due to “the security configuration and reduced attack surface [that] block this attack by default” in Windows 10 and 10 S.
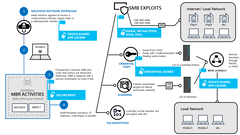
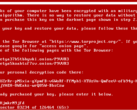
The analysis also points out that the ransomware software is exhibiting an ever-increasing sophistication and presents how the new Petya code was significantly more complex than previous ransomware codes. Petya employed a second exploit to promote lateral movement in networks, leading to increased propagation risks through networks that had an infected machine. The ransomware also featured a specific line of code that trashed boot sectors on Windows 7 computers protected with Kaspersky’s anti-virus (especially in the Ukraine).