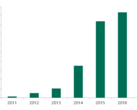
Two major ransomware, Locky and Mamba, that have been the subject of much discussion last year, have returned back to continue their onslaught on enterprises and gullible consumers. Locky first surfaced in 2016 and has been one of the most commonly distributed ransomware. Many variants of the ransomware exist and are spread via the Necurs and Dridex botnets. The current variant that is taking host systems for hostage is Diablo6. Diablo6 is currently prevalent in the United States and Austria. Indian businesses have started pressing the panic button after the attack hit systems in India this August.
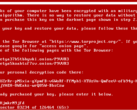
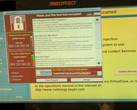
Locky is distributed via email spam campaigns that contain a subject line resembling 'E yyyy-mm-dd (xxx).docx'. The body of the email reads, "Files attached. Thanks." and contains the attachment 'yyyy-mm-dd (xxx).zip'. The ZIP file contains a VisualBasic script that connects to malicious domains to download and execute Locky Diablo6. There is also another email campaign that distributes a PDF file named similar to IMG_xxxx.pdf that contains a .docm file containing macros. If a gullible user opens the .docm file in Microsoft Word and enables the macro, the code downloads Locky from a malicious server. Once downloaded, Locky encrypts files using the RSA-2048 encryption algorithm and asks the user to install the Tor browser to visit the hacker's site for payment instructions. The user's files are encrypted with the .diablo6 extension and the hacker needs to be paid 0.49 Bitcoin (US$ 2079) to get a decryption key. Public decryption keys are currently not available.
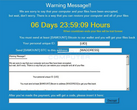
Mamba is the more lethal of the two as it encrypts the entire hard drive rendering the system totally unusable. Mamba seems to employ destructive tactics on large corporate establishments rather than extorting them for money. Last year, it managed to bring down the San Francisco Municipal Transportation Agency to its knees forcing the authorities to allow free travel until the computers were fixed. It has now resurfaced again in Saudi Arabia and Brazil in a more lethal form. The malware could spread via compromised websites or malicious email campaigns. Mamba utilizes the free Windows disk encryption software, DiskCryptor, to encrypt the entire hard drive of the victim. Once encrypted, the system reboots and displays a message on the screen asking the victims to write to 'mrcrypt2017@yandex.ru' or 'citrix2234@protomail.com' for the decryption key. There is no price asked outright for the decryption but the hacker decides the rate based on the number of computers affected.
2017 has been giving a hard time to cybersecurity researchers. First it was the WannaCry and Petya/NotPetya attacks that took large corporations to ransom and now older attacks are resurfacing in more lethal forms. We recommend that all users exercise caution while surfing the web and beware of suspicious email attachments or other communication asking for personally identifiable information. As always, take regular backups of your data and store them offsite. Make sure you secure your system with the latest OS/software updates and up to date antivirus software.