Securely sending messages has been a constant cat and mouse game between transmitters and intercepting parties. While modern messaging systems have several complex encryption methods, there is always a backdoor waiting to be opened. Researchers at Symantec have found one such backdoor in two popular secure messaging apps, WhatsApp and Telegram, that could allow a listening party to alter messages you see on your phone.
Currently, the exploit has only been found in the Android version of both apps. This is because the hole revolves around how Android apps store data once it has been received. In the case of WhatsApp and Telegram, if users enable the “Save to Gallery” setting (enabled by default in WhatsApp), the application will save incoming media into the Android file system’s external storage, which allows it to be intercepted by other applications.
To understand how to exploit works, looking at how Android saves data is needed. Android applications save files and data to either “internal” or “external” storage in the device’s storage. Internal storage can only be accessed by the application that saved the data there, while external storage can be accessed by any app or user with access to the device’s storage (known as “world-readable/writable”).
Android’s developer documentation points out that it is a best practice to store files that neither the user nor other applications should access in internal storage. Files that can/should be shared with other applications should be saved to external storage. As an example, an app-specific password should be saved to internal storage as no other application should need it for anything. Photo files should usually be saved to external storage as they will need to be read and written by the camera, a photo viewing app, a photo editing app, and any apps that can share photos.
By default, WhatsApp stores all received media in external storage. Telegram allows users to save media in external storage by enabling the “Save to Gallery” option. Herein lies the vulnerability.
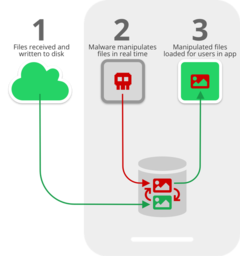
The researchers found that, properly coded, third-party applications could intercept media saved to the device via WhatApp or Telegram and alter or replace it before the user accesses it. The trouble is that the user’s device will receive media (e.g., a photo or a voice recording) in the application. If the option to store the media is enabled, the application will immediately write the media file to external storage, making it publicly available to all apps on the device. A malicious app could detect when media is received and stored and then alter or replace it. Then, when the recipient opens their application to see the media file, the altered file is loaded from external storage rather than the original.
The research team was quick to point out a few scenarios that could be used by attackers. Editing images in real-time with an advanced algorithm or replacing images outright could be troublesome for politicians running for office, advertising campaigns, or contracts sent as images. A more dangerous scenario involves payment ordered via a PDF invoice. In the example, the researchers were able to replace a bank account on an invoice with another account, which could result in funds being transferred to an attacker. The possibilities are nearly limitless thanks to advancements in AI; machines like DeepFake have shown that AIs can easily and quickly alter video and audio files into realistic frauds.
Symantec notified Telegram and WhatsApp about the vulnerability well in advance of publishing their findings. WhatsApp responded with the following:
WhatsApp has looked closely at this issue and it’s similar to previous questions about mobile device storage impacting the app ecosystem. WhatsApp follows current best practices provided by operating systems for media storage and looks forward to providing updates in line with Android’s ongoing development. The suggested changes here could both create privacy complications for our users and limit how photos and files could be shared.
According to their statement, it doesn’t appear that WhatsApp has any plans to change how media is stored at the current time. It should be noted that saving media files to internal storage may make them unusable or restrict the sharing of said files.
Android Q is planned to include a feature called Scoped Storage, which will restrict an application’s access to external storage and limit access to app-specific directories. While this will not fully mitigate vulnerabilities like those discovered in WhatsApp and Telegram, it will help to combat attacks by adding a few extra steps for hackers to circumnavigate. The best thing users can do is be fully aware of how their data is stored on their device and be conscious of what permissions have been granted to their applications.


 Deutsch
Deutsch English
English Español
Español Français
Français Italiano
Italiano Nederlands
Nederlands Polski
Polski Português
Português Русский
Русский Türkçe
Türkçe Svenska
Svenska Chinese
Chinese Magyar
Magyar