Public perception of OnePlus must be at an all-time low, with issues like inverted displays, emergency number dialing shenanigans, and the continued discontinuation of software support leading to unrest among fans of what used to be one of the most consumer-focused smartphone brands. The latest issue, one that proves OnePlus sends user data directly to its servers without permission, will do the company's PR no good.
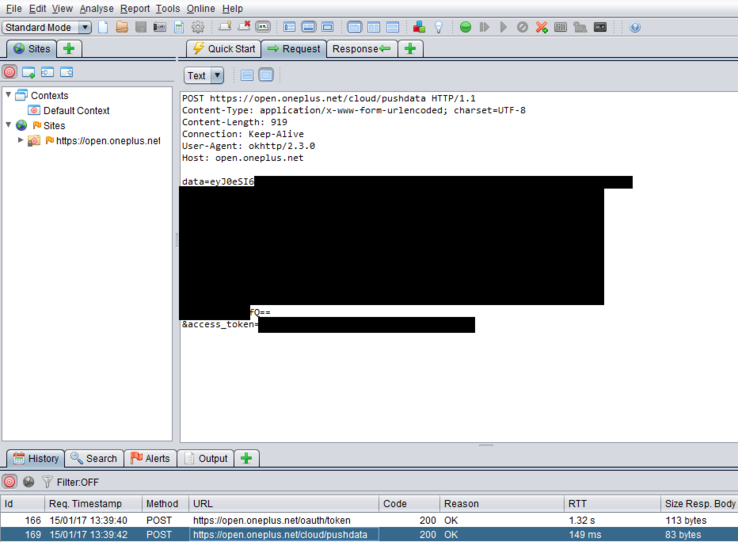
The finder of the data siphon, Chris Moore, owner of a UK-based security and tech blog, has outlined the methodologies behind him discovering the leak. Apparently, after hooking up his phone to a security tool, he found requests to OnePlus's "open.oneplus.net" domain. The information transmitted included:
- Reboot timestamps
- Charging timestamps
- Screen on/off timestamps
- Device firmware details
- Device serial number
- Device IMEI
- MAC address
- App processes and accompanying timestamps
All of these are damning details that compromise the user's security and privacy, and it's a bit shocking that such a large brand would do this without requesting for permission. Probably because no one in their right senses would grant permission to such an intrusive request, we expect.
While this may be a shocking move by the OEM, Android being open-source means that there are ways to stick it to them. You can either install a security tool like NetGuard and block off that domain, or freeze the transmitting apps (OnePlus Device Manager and OnePlus Device Manager Provider), if that doesn't mess up your ROM, that is, or simply block those apps from having access to your data. Better still, you could wipe OxygenOS off your phone and install a custom ROM like Lineage OS.
Shame on you, OnePlus.
Thanks to Reddit's vulgarly-named /u/PM_ME_D*CK_PICTURES for the tip!