23 Mar, 2017 | By Brian Duckering| SHARE THIS POST:
a:8:{s:4:”type”;s:7:”message”;s:12:”instructions”;s:0:””;s:8:”required”;i:0;s:17:”conditional_logic”;i:0;s:7:”wrapper”;a:3:{s:5:”width”;s:0:””;s:5:”class”;s:0:””;s:2:”id”;s:0:””;}s:7:”message”;s:17:”Block 3b: Detect”;s:9:”new_lines”;s:7:”wpautop”;s:8:”esc_html”;i:0;}
" data-medium-file="" data-large-file="" src="https://cg9j53d64gz46qncx41jvxq16p-wpengine.netdna-ssl.com/wp-content/uploads/2017/03/Q4ThreatRepot-WebThumbnail.png" alt="Click to read the full report." width="299" height="168">
Read the full report here
Skycure’s latest Mobile Threat Intelligence Report highlights that the vast majority of mobile device users could be more secure simply by updating to the latest security patches sooner. 71% of all Android users on the five major US carriers are running security patches that are at least 2 months old.
This report looked at mobile threat trends across all of 2016. Hackers are increasingly targeting mobile devices, but how are their tactics changing? By analyzing the data, and perhaps better understanding their methods and motivations, we can gain essential insight into the methods that will be successful in defeating their efforts and keeping our mobile data more secure.
The study looks at the evolution by quarter across the three major threat vectors – malware, network and OS/app vulnerabilities. Growth in malware and network incidents was substantial, but the majority of these malicious exploits depends on vulnerabilities in the operating system and core apps in order to succeed. Given that, we dedicated a section of the report to understanding how quickly security patches are adopted, because devices with known vulnerabilities that are unpatched are the most susceptible to breach.
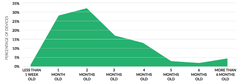
Apple’s iOS devices typically have a rapid adoption of security updates because the software, hardware and distribution mechanism are all tightly integrated. This is not the case for Android, which supports multiple hardware platforms and components across multiple mobile carriers, each who must create their own variation of the security patch before distribution. Here are the steps required to patch a mobile device, which helps to explain why most devices are running on two to three month old patches and many that could upgrade are running patches that are over 6 months old.
- Discovery of the vulnerability
- Notification to the developer
- Development of a successful patch
- Availability of each carrier-specific patch
- Distribution of the patch
- Installation of the patch
This is why the security patch adoption looks like this:
A loud and clear confirmation that this security patch deployment process is far from solved is Google’s 2016 Year in Review report which states “About half of devices in use at the end of 2016 had not received a platform security update in the previous year.” The US numbers revealed in the Skycure report are not nearly as bad as the global results from Google, but the security challenge and the window of vulnerability presented to attackers is still massive.
Because vulnerabilities are the root of the majority of mobile exploits, and patching them as quickly as possible is such a powerful way to reduce mobile risk, Skycure is proud to offer the only Android upgradability alerts in the industry. Only Skycure will alert on each individual device as security patches are available for that particular model from that particular manufacturer on the specific mobile carrier that has released the patch.
Other interesting trends revealed in this report include a shift in which types of malware are more popular. We found significantly increased incident counts for Hidden Apps, Trojans and Adware, while Potentially Unwanted, which started 2016 in the lead, finished in 4th place among the most common malware types.
Network incidents were also tracked, focusing on specific technology centers in the US. By the end of the year, the volume of network incidents was more than three times what it was at the beginning of the year, with massive increases in most locations – Boston topping out with almost a ten times increase. Three locations, San Francisco Bay Area, New York City and Portland, Oregon, stayed pretty flat across the year, with the Bay Area the only tech center that actually saw a slight reduction (by 13%) in overall network incidents.
Read the report to learn all about the shifting strategies and trends in mobile risks for enterprises, and install Skycure to minimize the window of vulnerability.