Cyber security firm, MWR InfoSecurity, has revealed the details of an Android bug which allows a rogue app to start screen recording without the user’s consent. This exploit was reported to Google back in January 2017 and is fixed in Android 8 Oreo, but Android 5 to 7.1 are still vulnerable.
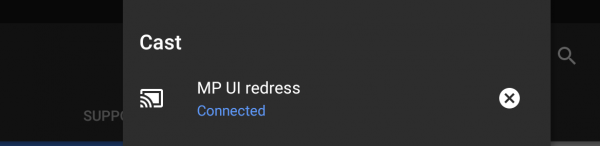
The exploit uses the MediaProjection service which allows developers to capture screen contents and record system audio without root access and has been part of the Android Framework since version 5.0. A screen recording can be started using a virtual module in the same way that an Android device might cast to a Google Chromecast.
Programmed behavior would involve a pop-up message asking the user for permission to start casting or recording, but this exploit consists in using a technique to draw an overlay on top of the pop-up requesting permissions, tricking the user into clicking a button which sits above the “allow” position on the original pop-up.
The recommended solution is to upgrade to Android 8.0, something which all Android users know is easier said than done on most devices which aren’t on a manufacturers upgrade list or don’t have good third party ROM support. The latest statistics regarding Android version adoption shows that 77.5 percent of devices are running one of the vulnerable versions of Android from 5.0 to 7.1.
Fortunately for those who can’t upgrade, the attack is detectable with a little vigilance. Because this method relies on creating a virtual display using the MediaProjection Service, it causes Android to show the screencast icon in the notification bar (the same one that you see when using a Chromecast). Therefore any sightings of this symbol when not using screencasting should be an immediate giveaway that something is amiss.