Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices

An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable. All vulnerable 2FA keys should be assumed compromised and replaced with non-vulnerable ones as soon as possible.
Two-factor (2FA) security authentication uses a unique code generated by a software app (e.g. Microsoft Authenticator) or a hardware key (e.g. Yubikey) in addition to a password to log into online accounts. A growing number of account providers, such as banks, have implemented 2FA security in order to reduce the theft of data and money.
Two-factor authentication keys depend on the generation of a unique code using methods that are difficult to reverse engineer. Modern 2FA apps and keys often use more complex math such as elliptic curve algorithms (deep dive into the mathematics at IBM's site).
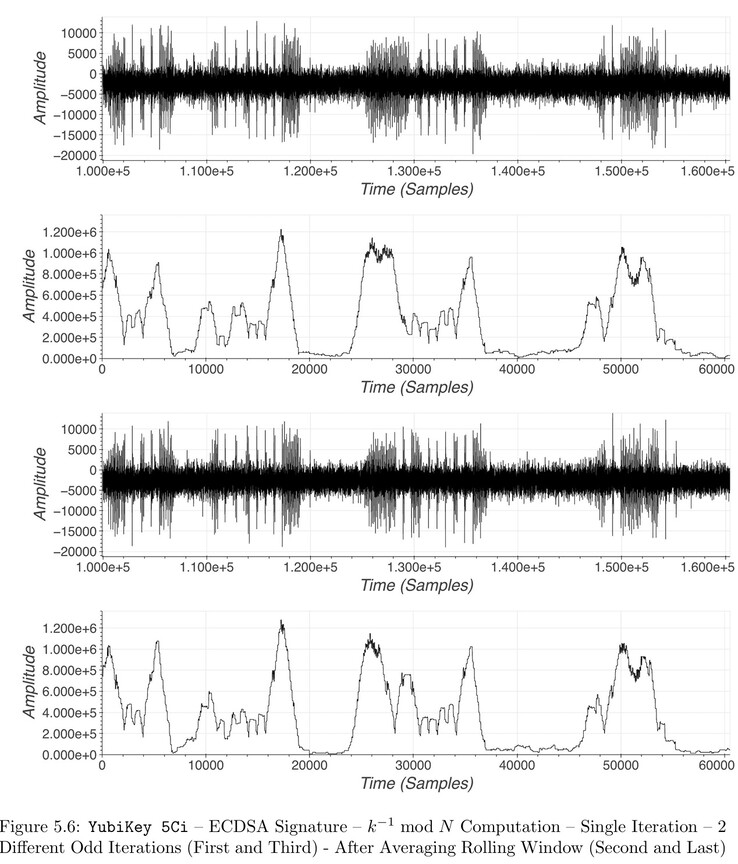
Side-channel attacks monitor aspects of an electronic device to create an attack. For the vulnerable Infineon TPM chips used in the Yubico, Feitian, and other 2FA keys, the researchers at Ninjalabs spent two years capturing and deciphering the radio emissions from the chips to create an attack.
Hackers would need up to an hour of access to the key to capture the radio emissions, then a day or two to decipher the data and create a copy of the 2FA key. The math and techniques are rather complex, so readers with know-how in cryptography, math, and electronics can read the complex methods in the NinjaLab's article. NinjaLab previously revealed similar vulnerabilities in other Google Titan, Feitian, Yubico, and NXP keys.
Users of Yubico 2FA keys should consult the Yubico security advisory to see if their keys are vulnerable. Users of other devices will need to ask the makers if the devices use vulnerable Infineon SLB96xx series TPMs. Affected devices cannot be patched to fix the security vulnerability.
All affected key owners should strongly consider switching to alternatives after confirming the alternatives are not vulnerable. Alternative 2FA keys include the Feitian or iShield.