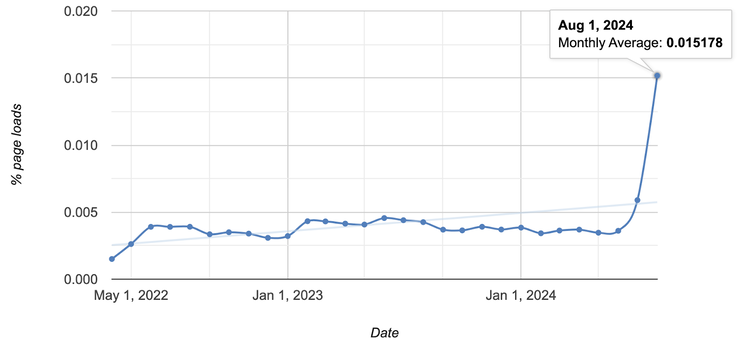
An 18-year-old vulnerability, known as the "0.0.0.0 Day" flaw, has been disclosed to allow malicious websites to bypass security protocols in major web browsers, including Google Chrome, Mozilla Firefox, and Apple Safari. The flaw primarily affects Linux and macOS devices, giving threat actors remote access, using which they can change settings, gain unauthorized access to sensitive information, and even achieve remote code execution. Despite being initially reported in 2008, the issue is still unresolved in these browsers, though developers have acknowledged the problem and are reportedly working towards a fix.
The "0.0.0.0 Day" vulnerability arises from inconsistent security mechanisms across different browsers and the lack of standardization that permits public websites to interact with local network services using the "wildcard" IP address 0.0.0.0. By leveraging this IP address, attackers can target local services, including those used for development and internal networks. "0.0.0.0" is often interpreted as representing all IP addresses on a local machine.
Researchers at Oligo Security have observed multiple threat actors exploiting this flaw. Campaigns such as ShadowRay and Selenium attacks are actively targeting AI workloads and Selenium Grid servers. In response, web browser developers are starting to implement measures to block access to 0.0.0.0, with Google Chrome, Mozilla Firefox, and Apple Safari all planning updates to address the issue.
Until these fixes are fully implemented, Oligo recommends that developers adopt additional security measures, such as using PNA (Private Network Access) headers, verifying HOST headers, and employing HTTPS and CSRF (Cross-Site Request Forgery) tokens, to protect their applications.