One might think that, with all the updates that have been released in the past 4 years, Windows 10 would be decently polished in the security department, but this clearly is not the case, as revealed by controversial security researcher SandboxEscaper. For some reason, Microsoft is still releasing updates that include zero-day flaws, and SandboxEscaper is exposing them before they get fixed. In the latest May update for Windows 10 alone SandboxEscaper managed to find three zero-day flaws, and even more will soon be unveiled.
Among the exploits, there is one that the researcher named AngryPolarBearBug2, which seems to be a new version of a flaw related to the Windows Error Reporting service discovered in December 2018. This new bug makes use of the discretionary access control list that is attached to objects found in the Active Directory. The list specifies which users and groups can access said objects and what kind of operations can be performed with them. SandboxEscaper notes that this exploit requires advanced skills and it may take up to 15 minutes to activate it, yet, upon successful trigger, the attacker can edit any Windows file and system executables.
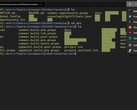
There is also a local privilege escalation bug which occurs in the Windows Task Scheduler. Attackers can’t directly break into systems via this exploit, but they can run a malformed .job file that can elevate initial low-privileges to admin access, granting total control over the entire system. SandboxEscaper released a video explaining how this works and pointed out that this exploit is only confirmed to work on 32-bit versions of Windows 10.
A third vulnerability was discovered within Internet Explorer 11, a web browser that is still included in Windows for legacy purposes, even though Microsoft is trying to promote Edge now. This type of exploit allows attackers to inject malicious code in the browser itself, making it easier for them to setup later attacks through exploit-chains.
SandboxEscaper is planning to unveil two more zero-day flaws and these will be posted on her blog and Github.
Loading Comments
I first stepped into the wondrous IT&C world when I was around seven years old. I was instantly fascinated by computerized graphics, whether they were from games or 3D applications like 3D Max. I'm also an avid reader of science fiction, an astrophysics aficionado, and a crypto geek. I started writing PC-related articles for Softpedia and a few blogs back in 2006. I joined the Notebookcheck team in the summer of 2017 and am currently a senior tech writer mostly covering processor, GPU, and laptop news.
> Expert Reviews and News on Laptops, Smartphones and Tech Innovations > News > News Archive > Newsarchive 2019 05 > Researcher reveals new zero-day Windows 10 vulnerabilities
Bogdan Solca, 2019-05-23 (Update: 2019-05-23)