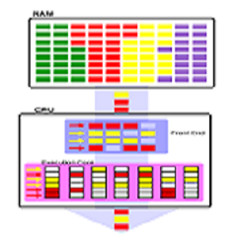
A team of researchers from the Tampere University of Technology in Finland and the University of Technology in Habana have reported the discovery of a new CVE which (again) affects Intel CPUs. This exploit has been classified as CVE-2018-5407, and is also known as PortSmash. It is another new side-channel exploit that leverages Intel Hyper-Threading (or simultaneous multi-threading (SMT)) to potentially steal data.
The Tampere/Habana team assert that the exploit can enable a hacker to run their process in a thread alongside a target process and steal from it, so long as they get the parallel-processing timing right. Accordingly, they have demonstrated the ability to steal a private SSL key from a TLS server using PortSmash.
The CVE has been confirmed as operable in Skylake or Kaby Lake CPUs, and could also affect other processors with SMT or Hyper-Threading. The work on PortSmash is to be found on GitHub and OpenWall, and will also be published in an upcoming article. Its authors suggest ensuring that OpenSSL is updated to a version later than 1.1.0i as a preventative measure against PortSmash. Intel has been informed of this issue, but is yet to respond (correct at time of writing).