The Nintendo Switch is undeniably one of the most popular gaming consoles on the market today, but it has a few drawbacks. A sticking point for several gamers has been the inability to backup save game files to any form of external media, meaning that if the console dies, so do the hours of save game data. Thus, the Switch has been a huge target for hackers. Earlier this year, we reported that one group (dubbed “fail0verflow”) successfully loaded Linux onto the console via a boot ROM bug. Now, a new group named “ReSwitched” seems to have found an “unpatchable” exploit to run arbitrary code on the Switch.
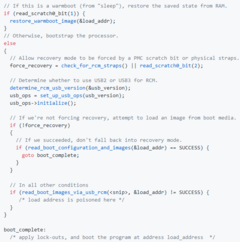
The vulnerability, posted recently on GitHub, details a method for running arbitrary code on the Nvidia Tegra line of processors’ Boot and power Management Processor (BPMP) before the chip can execute any lockouts. This, in turn, can allow a hacker to override the SoC’s USB software stack in order to run unsigned code before anything else can execute, opening any system using a Tegra chip to software hacking.
Essentially, any device that uses an Nvidia Tegra processor is vulnerable to the exploit, which includes the Nintendo Switch. Likewise, since the hack overrides the boot ROM embedded in the chip, it cannot be corrected by a software or firmware update; once the Tegra CPU has left the factory, it’ll be vulnerable indefinitely. There’s already a small device from fail0verflow in the works that might be able to short out the physical hardware in the Switch to allow for easier execution of the exploit. Shorting out specific pins in the right JoyCon’s connection rail will trigger the Switch to enter a USB recovery mode, which is the first step necessary to run the exploit.
Again, since the exploit occurs at the hardware level, there’s almost no way that Nintendo can prevent users from hacking their Switch consoles. This opens the door to piracy on the console, which is always a chief worry at Nintendo. There are a few ways that Nintendo can fight against pirates, such as detecting consoles that are running the exploit and banning them from online services, but the window for a fix from the gaming juggernaut is extremely narrow, if not permanently closed.
Before you run and grab your Switch to load Linux on it, there are a few caveats to keep in mind. The process is still extremely complex and shouldn’t be undertaken lightly. The ReSwitched team will release further details no later than June 15th, which should allow less code-savvy gamers to run the exploit. The hackers at fail0verflow have also stated that “it’s stupidly easy to blow up embedded platforms like this with bad software.” In other words, running an alternate operating system or other unofficial software could destroy your console.