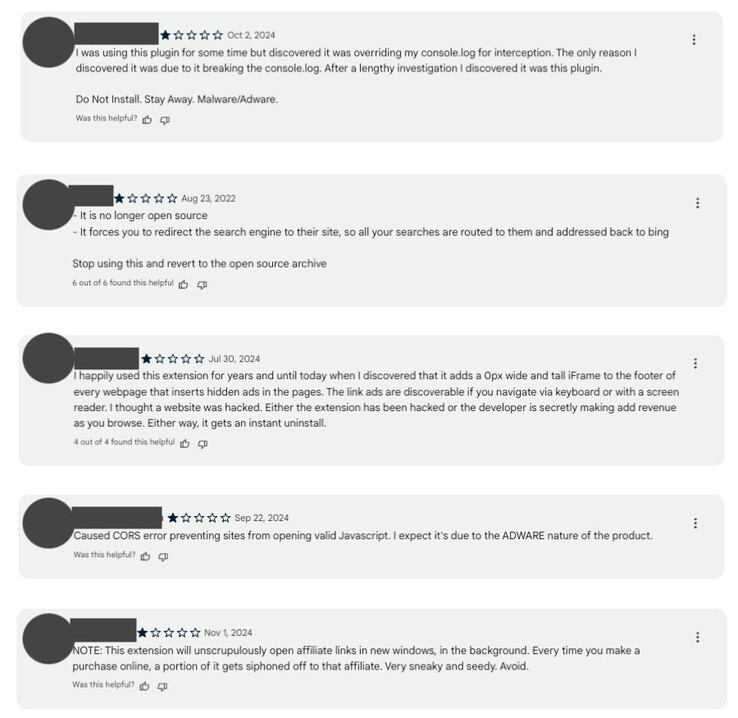
A major security breach has compromised over 3.2 million users through a network of malicious browser extensions. These extensions, which intentionally come off as legitimate, were found to be injecting harmful scripts, stealing data, and even engaging in search engine fraud. Researchers have determined that the attack was executed through a supply chain compromise, where the attackers infiltrated trusted extensions and pushed malicious updates without users even realizing it's happening.
The extensions in question were originally designed for ad blocking, emoji keyboards, and screen capture, to mention a few. However, updates introduced obfuscated scripts that enabled unauthorized data exfiltration, HTTP request modifications, and injection of advertisements into webpages. All these changes remained unnoticed by users who had earlier granted permissions to these extensions, which allowed attackers to manipulate web activity in real-time. Multiple security experts have pointed out that the permissions granted to these extensions, including host access and scripting controls, made them particularly dangerous.
Here's the complete list of all 16 affected Chrome extensions:
- Blipshot (one click full page screenshots)
- Emojis - Emoji Keyboard
- WAToolkit
- Color Changer for YouTube
- Video Effects for YouTube and Audio Enhancer
- Themes for Chrome and YouTube™ Picture in Picture
- Mike Adblock für Chrome | Chrome-Werbeblocker
- Page Refresh
- Wistia Video Downloader
- Super Dark Mode
- Emoji Keyboard Emojis for Chrome
- Adblocker for Chrome - NoAds
- Adblock for You
- Adblock for Chrome
- Nimble Capture
- KProxy
Investigations have traced this attack to compromised developer accounts. Some developers unknowingly ended up transferring control of their extensions to the attackers, who then distributed malicious updates through official browser extension stores. The infrastructure of this attack appears to be linked to previously known phishing operations. Threat actors achieved this by exploiting permissions such as 'host_permissions', 'scripting', and 'declarativeNetRequest'.
Another concerning aspect of this campaign is its resemblance to prior supply chain attacks, where attackers weaponize trusted software to spread malware. The use of browser extension update mechanisms lets attackers bypass traditional security measures.
For now, the identified extensions have been removed from official platforms. Regardless, users are advised not to rely solely on positive reviews before installing new extensions. Performing a mild background check on the developers of new extensions, and reading up on forums regarding the same could be a great first step to make sure that you're not falling victim to attacks such as these.