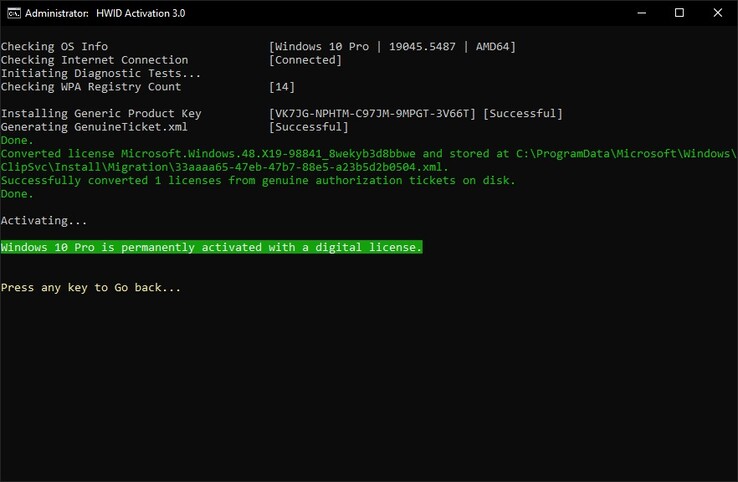
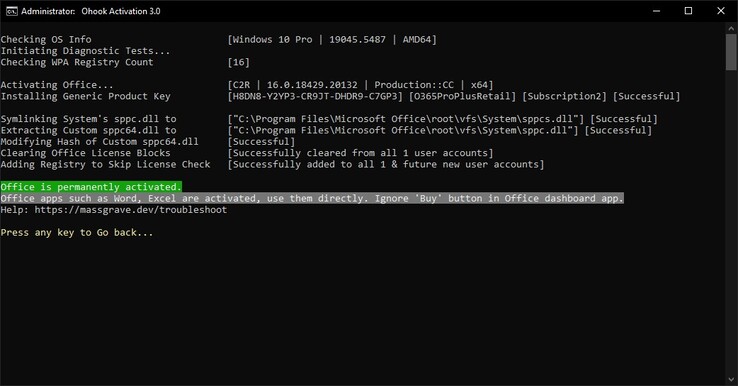
Microsoft's software activation system has long been a target for developers looking to bypass its restrictions, but a newly released activation method might just be it. A hacking group dubbed Massgrave has introduced TSforge -a tool that permanently activates Windows and Office products without requiring traditional validation. Unlike previous activation exploits, TSforge manipulates Microsoft's Software Protection Platform (SPP) at its core, since it inserts fake activation data directly into the system's trusted storage.
If you're wondering how this works, two key files in Windows’ activation framework are modified—data.dat and tokens.dat—which store product licensing information. By injecting forged data, TSforge forces the OS to recognize a fake product key or confirmation ID as legitimate. This allows Windows to remain activated indefinitely without needing online verification or periodic reactivation, making it an overall more robust solution than existing KMS-based activators. Some well-known KMS-based activators include KMSpico, KMSAuto Net, Microsoft Toolkit, and KMS VL ALL. These tools emulate Microsoft's Key Management Service (KMS) to activate Windows and Office temporarily, unlike TSforge.
Compatibility wise, TSforge supports Windows 7 and later, including Windows Server editions up to 2025. It also activates Microsoft Office versions from 2013 onward, provided they run on Windows 8 or newer. In addition to basic activation, TSforge enables features like Extended Security Updates (ESU) for older Windows versions and extends Windows 10 updates past the official October 2025 end-of-support deadline.
The activation method is now part of Microsoft Activation Scripts (MAS) 3.0, an open-source toolkit developed by Massgrave. Despite the scale of this DRM bypass, Microsoft has not publicly addressed the TSforge method or taken action against its distribution at the time of writing.