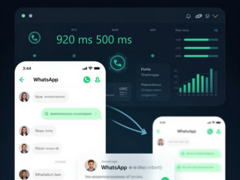
A group of researchers from the University of Vienna has found a small but serious security hole in the way end-to-end encrypted (E2EE) messaging services work. The study, initially published on November 17, 2024, under the title "Careless Whisper: Exploiting Silent Delivery Receipts to Monitor Users on Mobile Instant Messengers," highlights the possibility of tracking devices using Round-Trip Time (RTT) data when WhatsApp or Signal are installed.
A program has now been released on GitHub that can automatically exploit this vulnerability in WhatsApp. While the provision of such a tool raises ethical concerns, its purpose is intended to pressure WhatsApp into addressing the security gap and improving user privacy protections.
It turns out the basic idea behind that program is surprisingly simple. The tracker sends reaction messages to non-existent message IDs. The target device still replies with a delivery receipt. This reaction, invisible to the user, reveals the time required to send and receive the manipulated request—the RTT.
While these data points alone do not reveal an immediate location, they can provide valuable insights when collected over extended periods. Patterns within the RTT data can indicate when a device is actively in use or in standby mode. A network connection type, such as Wi-Fi or cellular, may also be deduced. By analyzing these activity patterns over hours or days, attackers could draw conclusions about user behavior. Furthermore, the constant requests consume battery life and mobile data on the affected smartphone.
Currently, users have limited options to defend against this tracking method. There are no notifications on smartphones alerting users to such monitoring. The attacker's phone number cannot be obtained, making blocking it impossible. Neither Signal nor WhatsApp currently offer an option to disable delivery receipts. A drastic solution is the only option at this time. Removal of all impacted end-to-end encrypted messaging services from your device.