An independent researcher called Patrick Wardle has made some worrying discoveries for those in possession of a brand-new Apple M1 MacBook Air, M1 MacBook Pro, or M1 Mac Mini. It appears users of those devices can already expect to be troubled by malware issues, as new examples of the accursed apps have been found. As reported by Wired, code that had been created for running on Intel x86 processors has been taken advantage of by shadowy types to come up with Mac malware that will operate natively on the Apple M1.
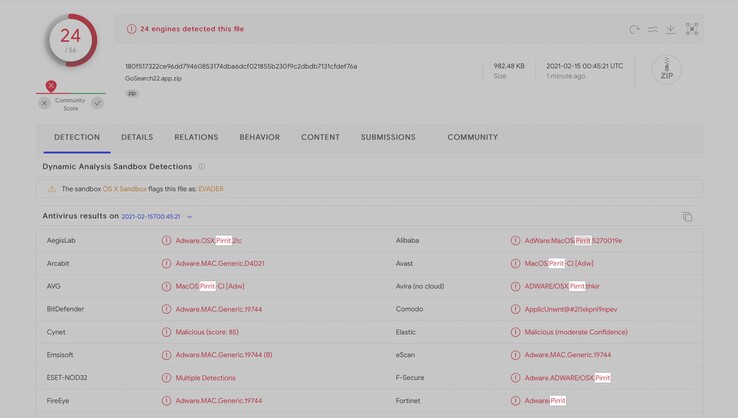
The GoSearch22 Safari browser extension has been specifically outed as a member of this new M1 malware family, with MacRumors explaining how this type of code can collect sensitive user data without permission and actually lead to more malware being installed on an infected machine. GoSearch22 has been associated with Pirrit-related ads, which when closed simply direct the user to a more-often-than-not malicious or dangerous website. Information for removing Pirrit can be found over at PCRisk.
GoSearch22 has already had its certificate revoked by Apple, but the discovery of the malware operating freely in combination with the company’s new M1 silicon will be disconcerting for future MacBook Pro/Air owners and security researchers alike. Apparently, the malware was difficult for anti-virus tools to weed out, with Wardle stating “detections of the arm64 version dropped roughly 15% (when compared to the standalone x86_64 version).” Just as developers have rushed to take advantage of the ARM-based M1 it seems so have malware coders.
Source(s)
Objective-See via Wired & MacRumors