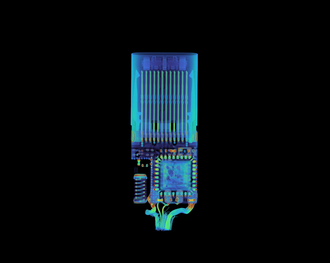
Lumafield, a company that specializes in imaging electronics and components, recently conducted a CT scan of the infamous O.MG cable. The results reveal how sophisticated hackers are in compromising unsuspecting users. Upon closer inspection, the O.MG cable, a seemingly normal USB-C cable, turns out to be a versatile tool for cyber criminals. They can use it to take over smartphones and PCs and steal sensitive data or install malware.
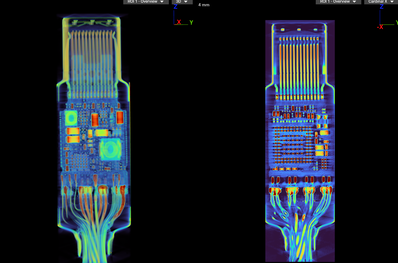
Lumafield's CT scans reveal the hidden technology inside the connector. A tiny microchip and an antenna are cleverly hidden in the normal-sized USB-C plug, which enable hackers to remotely access and control the connected devices. Lumafield has made the scans available online for interested parties.
Modern Thunderbolt and USB-C cables are complex structures equipped with electronics and chips in order to control data transfer, power supply and other functions. Even an X-ray image cannot clearly show whether a cable has been tampered with or not. The additional electronics in the O.MG cable are so small and cleverly integrated that they are almost indistinguishable from the regular components.
A few months ago, we reported (in German only) on the dangers posed by the O.MG cable and similar products. Hackers are now thinking more and more long-term, increasingly investing time and resources in projects that will bear fruit years later. This makes it all the more important to remain vigilant and be aware of the dangers.
Fake products that look deceptively similar to the original keep popping up on Amazon and other online marketplaces. For the layman, it is almost impossible to distinguish manipulated cables from harmless ones. So we can only hope that no hacker is actively selling cables with backdoors on Amazon.