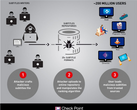
Armis Labs, an Internet-of-Things security company, informs that it discovered a Bluetooth vulnerability codenamed BlueBorne that can affect billions of devices, including Android and iPhone smartphones, Linux and Windows PCs, or even smart appliances like TVs, security cameras, medical devices and sound systems. This probably doesn’t come as a big surprise after all the CIA Vault 7 debacle. As if wanting to prove the Vault 7 suspicions, Armis also revealed 8 zero-day vulnerabilities that can facilitate the spreading of the BlueBorne vulnerability.
Google will issue patches for Android Nougat 7.0 and 6.0 as soon as possible. Among the widespread devices that could be affected by BlueBorne we find:
• Google Pixel
• Samsung Galaxy
• Samsung Galaxy Tab
• LG Watch Sport
• Pumpkin Car Audio System
The BlueBorne vulnerability is invisible to users and is able to spread from device to device on its own. Most operating systems confer high privileges to Bluetooth processes, and this enables the BlueBorne attack to spread through remote code execution, man-in-the-middle attacks, or penetration of air-gapped networks that are not connected to the Internet. In the wrong hands, this vulnerability could be used in cyber espionage, data theft, ransomware and the creation large botnet networks made of IoT devices.
According to Armis, airborne attacks like BlueBorne show a new type of threat that is most of the times ignored by traditional security solutions. If air-gapped networks get breached, the attack can endanger industrial systems, government agencies, and critical infrastructure. The dispersal power of this attack is facilitated by the feature that makes Bluetooth enabled devices constantly search for other Bluetooth devices. Armis warns that current security measures such as endpoint protection, mobile data management, firewalls, and network security solutions are not designed to deal with airborne attacks, because their main focus is to block attacks that happen over IP connections.
Since most users are still using older devices that will probably won’t get any patch for the BlueBorne vulnerability, the best way to avoid the attacks is to permanently disable the Bluetooth connection, and only enable it when needed.