There have been several cases in the last couple of months of the Coinhive cryptomining code being used for nefarious purposes. Generally, it involves the code being implanted in an unsuspecting website or plugin and using visitor’s CPU cycles to process cryptocurrency transactions. Websites administrators can also implement the code directly themselves.
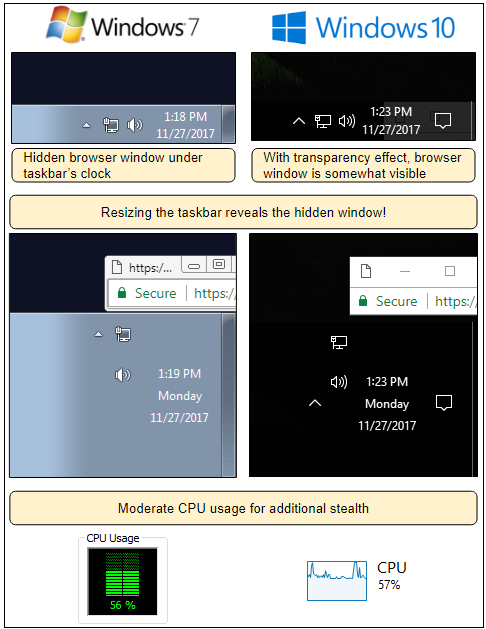
Until recently it was a safe assumption that once the offending website is closed — or the browser is shut down — the mining will stop, and the CPU load will disappear. Malwarebytes has now uncovered a method which allows attackers to create a pop-under that hides a compact browser window underneath the clock in the taskbar. When the main browser window is closed, the hidden window continues to process the cryptomining code unbeknown to the user.
Malwarebytes observations were that once a website using this method is visited the drive-by cryptomining starts. CPU activity rises noticeably (using an unidentified dual-core/non-HT CPU) but leaves enough headroom that other than an increase in fan noise the user might not notice anything unusual, once the browser is closed the high CPU activity continues unless the pop-under is found and terminated.
This method also acted in a way that bypassed adblockers and the stealth way in which it appears means that using task manager or another program designed to monitor processes are a good way to identify if any remnants of the browser remain active (users can also check for the active window icon in the taskbar). This testing was all performed using Google Chrome and although Malwarebytes says that experiences might be different using other browsers, it would stand to reason that any browser which allows the creation of a separate compact window in the background could allow this attack method.
We recommend visiting the original Malwarebytes report for additional details and explaination.