Just a few days ago news broke that The Pirate Bay had embedded a cryptocurrency mining script within their website code, which was using visitor’s CPU cycles to generate revenue instead of using traditional advertising. Theirs was a 24-hour trial, and the script has been removed and the original advertising reinstated.
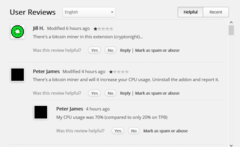
Earlier today a new version of the free Chrome extension, ‘SafeBrowse,’ was also found to have the same cryptocurrency mining script from CoinHive embedded in its code. Users started leaving one-star reviews and posting on Reddit shortly after the extension was updated, complaining of high CPU usage in the 60 to 100 percent range. The current version showing on the Chrome Webstore is 3.2.25, which appears to be the affected version.
BleepingComputer tested the extension themselves and found that “The impact on our test computer was felt immediately.” The extension itself used over 60 percent of their CPU cycles, and the overall CPU utilization would jump between approximately 70 to 100 percent. Usage remained high for the entire time that Chrome was open, and only closing the browser (or presumably disabling the extension) would let things return to normal. Like the incident with The Pirate Bay, it is an interesting way to gather revenue in place of advertising, but SafeBrowse has made the same mistake of implementing it without notifying users. Also, the script is configurable, and they appear to have it set to one of the more resource hungry modes with one user complaining that their CPU usage was around three times higher than when they visited The Pirate Bay.
SafeBrowse is currently installed on slightly over 140,000 machines, and despite the name, it isn’t a security-focused plugin. It is designed to by-pass linking services such as adf.ly where you must view an advert for a few seconds before continuing, so it can be disabled or removed without compromising user security.
Loading Comments
I grew up in a family surrounded by technology, starting with my father loading up games for me on a Commodore 64, and later on a 486. In the late 90's and early 00's I started learning how to tinker with Windows, while also playing around with Linux distributions, both of which gave me an interest for learning how to make software do what you want it to do, and modifying settings that aren't normally user accessible. After this I started building my own computers, and tearing laptops apart, which gave me an insight into hardware and how it works in a complete system. Now keeping up with the latest in hardware and software news is a passion of mine.
> Expert Reviews and News on Laptops, Smartphones and Tech Innovations > News > News Archive > Newsarchive 2017 09 > A Chrome extension now takes your CPU cycles to mine cryptocurrency for the developer
Craig Ward, 2017-09-19 (Update: 2026-02-18)