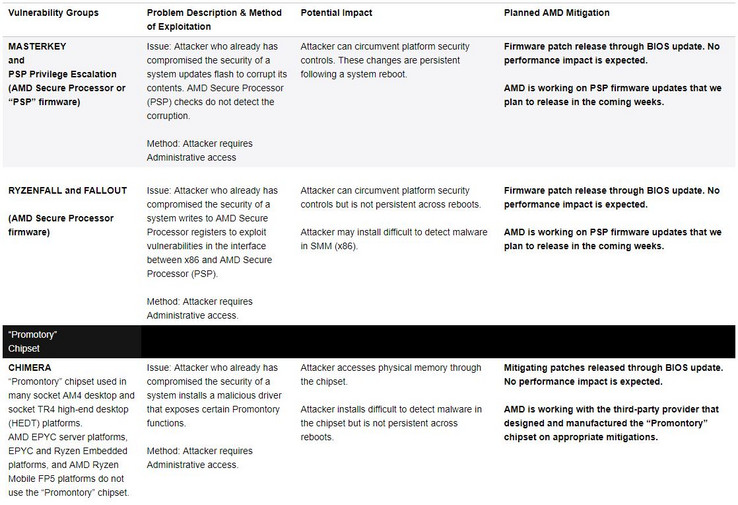
Last week, security research company CTS Labs reported its findings regarding 13 critical vulnerabilities that come with AMD’s Ryzen and EPYC processors, and demanded to get a response from AMD in just 1 day. CTS Labs also refused to provide details on each vulnerability, raising suspicions regarding the authenticity and the nature of its report. After more than one week, AMD is finally taking an official position with a blog post informing that all the issues reported by CTS Labs can and will be fixed in the coming weeks.
Here are the most important aspects presented in the AMD response post:
• The new exploits are not related to the Meltdown/Spectre vulnerabilities
• All 13 exploits can only be reproduced with admin access on the affected system
• The vulnerabilities are related to AMD’s Secure Processor firmware and its impact on some socket AM4 and TR4 desktop platforms
• Since the exploits have nothing to do with the microarchitecture itself, AMD will only release BIOS updates with firmware patches via OEMs and ODMs
• The fixes will not impact performance in any way and will be released in the coming weeks (90 days or less)
AMD had its share of troubles with the Meltdown/Spectre vulnerabilities and the consequent lawsuits, but it seems the company managed to tackle the CTS Labs debacle fairly well, as these new vulnerabilities are not hardware-related. However, AMD will most likely follow Intel’s footsteps by implementing hardware fixes for the Meltdown/Spectre vulnerabilities in its upcoming CPU models.
Loading Comments
Previous article
Windows Server 2019 Preview now availableNext article
QNAP launches the AMD-powered TS-x73 NAS lineupI first stepped into the wondrous IT&C world when I was around seven years old. I was instantly fascinated by computerized graphics, whether they were from games or 3D applications like 3D Max. I'm also an avid reader of science fiction, an astrophysics aficionado, and a crypto geek. I started writing PC-related articles for Softpedia and a few blogs back in 2006. I joined the Notebookcheck team in the summer of 2017 and am currently a senior tech writer mostly covering processor, GPU, and laptop news.
> Expert Reviews and News on Laptops, Smartphones and Tech Innovations > News > News Archive > Newsarchive 2018 03 > AMD acknowledges CTS Labs exploits, will fix them in the next weeks
Bogdan Solca, 2018-03-21 (Update: 2018-03-21)