Researchers at Russian cybersecurity firm Kaspersky recently presented detailed findings from Project Triangulation, their ongoing investigation of an iOS malware attack that they say is “the most sophisticated” they have ever seen. First reported in June 2023, after being discovered on some of the company’s own devices, the malware was found to have compromised devices since 2019, and was designed to work on iOS versions up to 16.2. The company’s CEO Eugene Kaspersky has described it as “an extremely complex, professionally targeted cyberattack”.
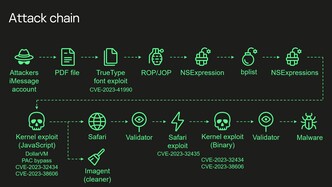
The findings reveal that it exploits four zero-day vulnerabilities (i.e. inherent security flaws in a system) in the iPhone, including bypassing Apple’s hardware-based memory protection, to obtain root level access and install spyware. Although not officially attributed to any specific party, it was alleged by Russia’s FSB that the malware is the work of the American NSA working in collaboration with Apple to hack the phones of Russian diplomats and other individuals.
The attack begins with a message received via the iMessage service, containing an attachment. Being a zero-click exploit, the message requires no user interaction to begin its work. The attachment exploits a series of zero-day vulnerabilities, first to trigger remote code execution, and ultimately leading to the malware gaining full control over the device. This includes the ability to read/modify/delete any files, extract saved credentials and passwords, monitor live device geolocation, and clean up its own tracks (including deleting the original message).
A significant discovery in the latest report was of a mysterious hardware feature in Apple’s SoC (now recognised as CVE-2023-38606), which allows the attackers to “write data to a certain physical address while bypassing the hardware-based memory protection by writing the data, destination address, and data hash to unknown hardware registers of the chip unused by the firmware.” The feature was either left in accidentally or is used for factory debugging, but since it is never actually used by the firmware, it’s not clear how the attackers learnt of its existence and how to exploit it.
Even though the attack so far seems to have targeted iOS versions up to 16.2, and a number of the vulnerabilities have since been patched by Apple, there is evidence that the malware had been updated at least once for newer iPhone models and iOS versions. For now, the best defence seems to be staying updated with the latest iOS version. Since the malware’s code is deployed in the memory, rebooting does erase it, but the device can always be re-infected if the attacker resends the message.
Kaspersky is close to completing the reverse-engineering of this attack chain and will share further details in coming months. Its latest report concludes by stating that “advanced hardware-based protections are useless in the face of a sophisticated attacker as long as there are hardware features that can bypass those protections…Hardware security very often relies on ‘security through obscurity’...but this is a flawed approach, because sooner or later, all secrets are revealed.”
Secure your private data with the Kingston IronKey Vault 960GB external SSD with 256-bit encryption, or the Lexar Jumpdrive Fingerprint 64GB USB 3.0 flash drive