How secure processors help protect confidential data
Companies are constantly under attack from cyberattackers. According to the eco Association of the Internet Industry, a fifth of German companies had at least one serious security incident in the past year. The Federal Office for Information Security (BSI) describes the IT security situation as "tense".
No wonder: Cyber criminals are constantly using new complex and sophisticated attack patterns and malware to attack IT infrastructures and access sensitive company data. But it's not just about software and operating systems. Increasingly, hackers are also targeting hardware and firmware. They exploit vulnerabilities to manipulate the firmware or to read data that the computer is processing in the system memory. This includes passwords, character strings used for encryption or other access codes. With this, the hackers can simply log into the system and access stored data. Encryption of the hard disk or other software-based protection mechanisms are thus nullified.
More security through hardware and software-based protective measures
Hardware-based security features are therefore increasingly complementing the existing software-based defense measures. A combination of both protection levels, which complement each other and protect the system from complex and dynamic attacks, is ideal. The goal: to secure the data on the computers of companies and users.
AMD has developed its "Zen" architecture for special security mechanisms: These should protect user data and at the same time ensure high performance. The architecture is the basis of the manufacturer's Ryzen™ and EPYC™ processors, which are found in PCs, workstations, and servers, among other things.
Every AMD processor has an integrated security technology: In addition to the actual architecture, a dedicated hardware security chip also works in it. This AMD Secure Processor (ASP) has several advantages:
- Hardware-based security can isolate critical processes and data in order to better protect the entire platform - including against attacks on the firmware.
- The processor with security functions can authenticate the firmware loaded at startup. Manipulated or incorrect firmware is then prevented from executing or access is denied.
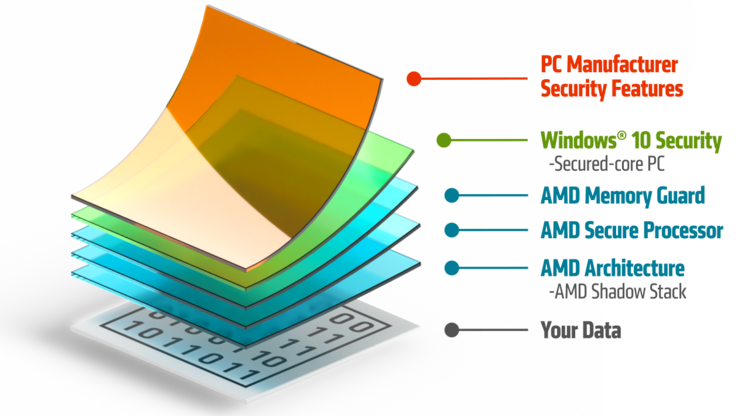
- Only when the firmware and BIOS have been authenticated does the processor transfer BIOS control to the operating system. Each layer of the security infrastructure complements the next, which increases the level of protection.
AMD develops its features at the silicon and firmware level together with manufacturers of hardware and operating systems. The respective protective measures at different levels can thus interlock. This enables security functions at enterprise level or secured core PCs, i.e. a Windows 10 device with the highest hardware, software and identity protection.
The AMD Shadow Stack is also integrated into the architecture of the powerful PRO processors of the Ryzen 5000 series. This is a hardware-supported defense against so-called control flow attacks - i.e. certain malware attacks directly on the CPU.
The risk of cold start attacks for the system data
But the stored data is not only threatened by the Internet. In the US alone, a laptop is stolen every 53 seconds. Employees can also lose devices or intruders can enter the company building. The problem: computers are often not switched off completely, but remain in standby mode. They are then ready for use again in a few seconds, including all previously opened programs and documents.
While this is easy to use and convenient, it poses a security risk. Because when a user logs in, a lot of important system information is stored unencrypted in the DRAM. A physical attacker can freeze this memory, reset the system, bypass the erase functions and then read out the DRAM contents.
Such a cold start attack cannot be prevented by security mechanisms such as encryption of the hard disk. One way to protect yourself is to shut down your computer completely. However, this annoys employees and slows down productivity because booting takes time. But there is another way to prevent such attacks and thus protect data.
The encrypted system memory prevents access
All AMD Ryzen PRO processors bring an additional layer of protection for the computer. The integrated safety coprocessor ASP forms the basis for the AMD Memory Guard. This is an additional layer of encryption that encodes the system memory. This happens directly in the memory controllers on the chip and with the help of a random key. In this way, attackers cannot read out the system memory and gain access to passwords or other access data.
With the AMD Memory Guard, physical cold start attacks, DRAM interface snooping and similar attacks can be fended off. At the same time, users can comfortably use the computers because they do not have to be shut down. The AMD Memory Guard is transparent for the operating system and applications and can therefore be installed and used on any system.
Conclusion
With its multi-layered security approach, AMD Ryzen PRO processors protect sensitive data on company computers from attackers from the Internet and on-site. This also reduces downtime - and ultimately lowers operating costs.
- Learn more about AMD Ryzen™ PRO here:
www.amd.com/en/products/ryzen-pro-processors-laptop