Researchers from security firm, Positive Technologies have just stumbled upon something truly phenomenal. They have found a method to disable the much hated Intel Management Engine (ME) in a way that still allows the computer to boot up. This discovery could potentially secure many businesses and state institutions from being compromised by highly sophisticated malware.
What is the Intel ME anyways?
The Intel ME is an embedded processor that is part of every Intel Platform Controller Hub (PCH) and runs its own full fledged OS. Think of it as an extra computer within your computer that runs its own firmware. You cannot choose not to have the ME — it comes part of every Intel x86 CPU and chipset and runs independent of the main CPU and the OS. It can also run in the suspend (S3) power state. Therefore, the activities of the ME cannot be audited. The ME implements something called Intel Active Management Technology (AMT) that is capable of accessing any memory address unbeknownst to the main CPU. Since it runs a complete OS in itself, it can run its own TCP/IP server completely bypassing any installed firewall. The ME was originally intended as a way to allow sysadmins to remotely administer and maintain computers.
What makes it a security concern?
The ME firmware is encrypted with an RSA 2048 algorithm. Despite that, experts have found ways of exploiting the ME firmware and take partial control of the ME and thereby, the computer. As mentioned earlier, the activities of the ME are not audited as it is invisible to the OS. Therefore, any attacker employing a rootkit exploit on the ME firmware can potentially take control of the remote computer and wreak havoc without being detected. As such, the ME has garnered a reputation for being a backdoor and a potentially powerful rootkit mechanism, earning a Ring -3 vulnerability for itself. Researchers have been trying to disable the ME but due to Intel's secrecy of the code and storing it in a non-standard compressed format that needs a hardware decompressor, most of the efforts have been unsuccessful. Any attempt to tamper with the ME firmware has resulted in PCs either refusing to boot up or shutting down immediately after boot as the ME code directly affects the initiation of the main CPU. Currently available methods only serve to slim down the ME firmware but do not completely disable it. As documented by Microsoft, there is an espionage group that exploits the TCP/IP server of the AMT to remotely execute malicious code. A recent vulnerability, CVE-2017-5689, has also been disclosed necessitating the need to address the ME loophole at the earliest.
How could they disable it?
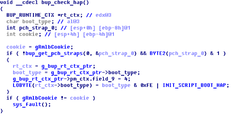
Security research firm, Positive Technologies has finally been able to fully disable the ME. They discovered a hidden bit in the firmware code, which when set to '1' disables the ME after booting up the main CPU. The bit is called 'reserve_hap' and is described in the code as 'High Assurance Platform (HAP) enable'. The HAP is a program by the NSA that lays out a series of rules that vendors should invariably stick to, in order to be approved for secure computing applications. The researchers believe that NSA's rules could have compelled Intel to include the switch as a way to ensure security compliance in institutions dealing with highly sensitive data.
What is Intel's take on this development?
Intel has been denying (obviously!) allegations that the ME could be a highly latent backdoor. The company has responded to Positive Technologies' breakthrough by saying,
"In response to requests from customers with specialized requirements we sometimes explore the modification or disabling of certain features. In this case, the modifications were made at the request of equipment manufacturers in support of their customer’s evaluation of the US government’s “High Assurance Platform” program. These modifications underwent a limited validation cycle and are not an officially supported configuration."
What is Positive Technologies' take?
The security researchers who have figured out how to disable the HAP bit do warn that the hack is not fully tested and can potentially brick a lot of systems if not performed under the guidance of a Serial Peripheral Interface (SPI) programmer. The research firm also notes that there are still some more mysteries to be solved with respect to how the HAP bit sets the Boot Guard policies in the firmware.
What can end users do?
The Intel Management Engine allows admins to remotely control PCs on the network and it houses a full OS in its firmware. Vulnerabilities in the firmware code have been doing the rounds ever since the first Core 2 chips were launched in 2006. Updates to the ME firmware are not released via conventional OS update mechanisms and the user is left to the mercy of Intel and its motherboard partners to provide the requisite firmware updates. Although all modern PCs running Intel's chips are a theoretical risk of being compromised, exercising due diligence can still win half the battle. The other half is dependent on how Intel addresses the issue going forward.