DDR5 is currently the fastest RAM standard for mainstream computers and it has seen availability for around 5 years. While RAM vulnerabilities can be forced on any type of standard, it looks like DDR5 may be more prone to malicious attacks than previously thought. Researchers at the ETH Zurich University in Switzerland teamed up with Google security experts and managed to create a DDR5 Rowhammer attack variant dubbed Phoenix, which can take advantage of the higher read/write speeds to access memory cell rows and flip the value of nearby bits from 1 to 0 and vice-versa. The attack was performed only on DDR5 modules with SK Hynix chips. Presumably, this could affect all DDR5 chip brands.
SK hynix implemented a standard Rowhammer defense mechanism called Target Row Refresh (TRR) that prevents bit flipping through extra refresh commands when unusually frequent access to particular rows is detected. The researchers of the Computer Security Group from ETH Zurich teaming up with Google security experts managed to reverse-engineer this security measure. It thus became apparent that certain refresh intervals were not protected so the researchers came up with a way to track and synchronize with the multitude of TRR refreshes and even self-correct when a missed refresh is detected.
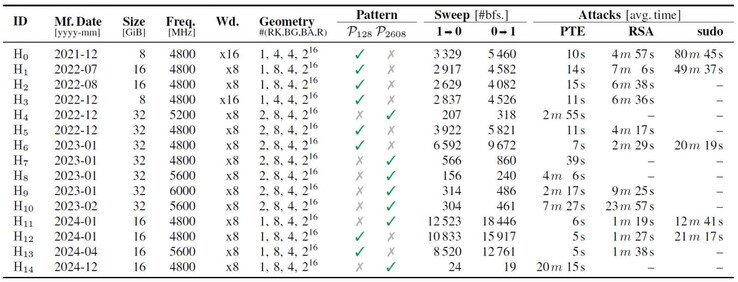
As such, the researchers determined that only 128 (more effective) and 2608 refresh intervals would allow for the new Phoenix attack to work. Applying this method, a shell with root privileges was compromised in less than 2 minutes. During the extensive practical exploit scenarios conducted by the researchers, it has been found that all SK Hynix products were vulnerable to page-table entry (PTE) targeting, while 73% of the DIMMs were vulnerable to RSA-2048 key SSH authentication breaks, and only 33% of the modules were affected by sudo binary alteration for root level access.
The Phoenix exploit received a high-severity score and affects all RAM modules with SK hynix chips produced between January 2021 and December 2024. It is still unclear what other brands with associated production times are affected. There is a solution for the Phoenix attack that involves the activation of the tREFI spec (triple DRAM refresh interval) on affected RAM modules, but this is not really recommended as it can produce more data corruption errors resulting in BSODs and general system instability.