Cybersecurity researcher Nati Tal, head of Guardio Labs, has highlighted a new Grok AI exploit that allows threat actors and scammers to bypass link restrictions on promoted posts and spread malicious links on X.
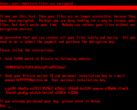
The method called "Grokking" involves hiding a link in the From field of a promoted post and then asking Grok to find the source of the paid boost. Grok finds the link in the From field and includes it in its reply, unwillingly boosting its discoverability.
According to Tal, this works because Grok's X account is "system-trusted" and not liable to checks or scrutiny. Worse, these paid posts are boosted for engagement and receive "100k to 5M+ impressions" with Grok's reply beneath them.
Invoking Grok to answer also boosts the SEO and "domain reputation", since it was "echoed by Grok on a post with millions of impressions!"
According to Tal, the links "lead through shady ad networks, monetizing clicks with "direct links" that are known to push Fake captcha scam, Info stealer malware and other shady grey-area content." Tal says this method makes the links "fully visible, clickable, and impossible to miss."
The posts themselves are disguised as "video card" posts with attached "adult content baits" that somehow make it through X's review. Tal also asserts, "There is no malicious link scanning whatsoever on X! Yet, it is still barely noticeable at this spot."
Funnily enough, Grok responded to a user just below the post and served a broken link when asked for the correct link to report the issue.