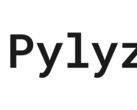The Windows application of the well-known messenger Telegram contains in its source code a list of file extensions for which a security warning is issued when such a file is clicked on. This includes, for example, Windows executable files, for which the Telegram Windows application issues the following warning "This file has the extension .exe. It could damage your computer. Are you sure you want to run it?
Such a dialogue should also appear for executable scripts in the Python programming language with the extension .pyzw. However, a typing error (".pywz" instead of ".pyzw") meant that no warning appeared for Python zip archives, but the code was executed directly after clicking on a link, provided that a Python interpreter was available on the Windows system. If such a Python script is now obfuscated with the file type "video/mp4", for example, the executable will appear as a video in Telegram Messenger.
Server-side workaround already available
In a statement to Bleeping Computer, Telegram's developers said: "There was [...] an issue in Telegram Desktop where the user had to CLICK on a malicious file while the Python interpreter was installed on their computer. Contrary to previous reports, this was not a "zero-click" vulnerability that could only affect a tiny fraction of our users: Less than 0.01% of our users have Python installed and use the corresponding version of Telegram for Desktop".
The typo in the source code on GitHub has already been fixed by the Telegram team, but an updated Windows app with the corrected code is not yet available. However, the developers of the Telegram messenger have also implemented a server-side fix, which means that Python script archives will no longer be executed directly on Windows, even in older versions with the bug in the code, but a warning will be displayed as with EXE files.


 Deutsch
Deutsch English
English Español
Español Français
Français Italiano
Italiano Nederlands
Nederlands Polski
Polski Português
Português Русский
Русский Türkçe
Türkçe Svenska
Svenska Chinese
Chinese Magyar
Magyar