FAQ: Security Solutions for Notebooks
For the original German review, see here.
It can be information as secret as the intelligence of the secret service: Company data. Unauthorized access to the hard drive of a notebook or the server of a business can have terrible repercussions, and in some cases it can even put the life of the company in jeopardy. In light of that, when selecting a notebook for business use, security is a top concern. Simple password protection upon the start-up of a computer doesn't constitute much of a hurdle for many offenders. Even if the thief doesn't know the password, there is still a high chance of him or her getting their hands on sensitive data. This is especially true if the creator of the password was inexperienced and naive in choosing the password. If the creator uses standard phrases or chooses the name of their wife, children or pet, often a little experimentation is enough for the thief to break through to the data. There is demand, then, for security that functions even if the user fails.
Smartcard as a Key

One approach to better data protection is the use of Smartcards. A Smartcard is, as the name suggests, a "smart" card that acts like a key. It contains stored information or can even have its own processor. EC cards and access cards for doors are examples of this technology. Identification is often confirmed by the use of a security code in conjunction with a smart card. The card then releases its information only after this code is entered correctly. Important: The data should be locked on the Smartcard so that it cannot simply be read and used. Not every Smartcard guarantees that.
If access to a notebook is dependent on a Smartcard, the computer checks the data on the Smartcard against data on the computer and only gives the user access to the notebook if the data agrees. It is also possible to set a Smartcard so that data can only be used if the proper card is present. This data can be saved encrypted and only become unencrypted while the Smartcard is active. The notebook must have the proper reading device to recognize the Smartcard. It's best if the reading device is integrated into the case of the notebook, but there is a version that can be retrofitted to a PC card or ExpressCard slot. There are also special USBs that function similarly to a Smartcard -- they also contain important access data on their stick. Without that data it's a no go. A pro in comparison with a Smartcard: No special reading device is necessary. There are USB ports on practically every notebook. Software also exists that can convert SD cards into Smartcards. Such solutions free up that otherwise occupied USB port, though there must be an SD card slot on the notebook. An SD card slot is however standard for modern notebooks.
Pros taken into account, there are also some cons to using a Smartcard to increase data security. If the user leaves the Smartcard in the device and walks away, or if he or she carries around the Smartcard with its access code in the same bag as the notebook, the protection is lost. In this case the human factor can easily undermine the protection. Just as problematic: If the user forgets to take the Smartcard along, he or she will not have access to his or her own data.
Fingerprint Scanner
An alternative that sidesteps the aforementioned cons of the Smartcard is the fingerprint scanner. If a fingerprint scanner is present and active, it prohibits anyone from entering the system unless the correct fingerprint is scanned and recognized. This kind of a system is easy to use and effective. In addition to freeing the user from having to carry around a Smartcard, a fingerprint scanner saves the user the hassle of a password, which must be remembered and periodically changed. For security purposes it's important that the fingerprint image data on the hard drive is encrypted.
Possible cons of this solution: In some cases it takes several tries before a fingerprint is read correctly. Also, a fingerprint scanner should be built into the case of a device, since retrofitted versions take up unnecessary space and make the scanner awkward to use. Tip: Save one of the fingerprints from your other hand just in case. Then you will still be able to access your computer if you are injured and your finger is covered by a band-aid or plaster.
But don't use a fingerprint scanner as your only measure of security. The reason: Many of these recognition systems can be outwitted fairly easily. Sometimes it's enough to lay a printed image of the fingerprint on the scanner to gain access to the computer. For others all a thief would need to do is copy a fingerprint off of an object using plastic wrap, stick the plastic on one of their fingers and hold it on the scanner.
TPM - Trusted Platform Module
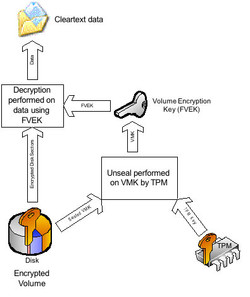
Another very good alternative is the Trusted Platform Module, TPM for short. The TPM is a chip that is securely soldered into the motherboard. The security keys needed to encrypt and unencrypt data are saved onto this chip. It also contains digital signatures and information identifying the computer, so that the computer is able to gain access to a network. TPM modules have been common in business notebooks for some time now, but rarely used in notebooks for private users. In contrast to Smartcards and fingerprint scanners, which identify the user of a notebook, TPM identifies a computer with another computer. Among other things, TPM is used in the encryption program BitLocker, which is a component of some Windows operating systems. By default the tool only functions when the corresponding chip is on the motherboard -- though it can be convinced to activate without the chip if a corresponding USB stick is present. A potential problem with the latter possibility is that without the proper USB stick, the data on the computer is inaccessible. Microsoft integrated BitLocker into its Ultimate and Enterprise versions of Windows Vista on up, and its Pro and Enterprise versions of Windows 8.
If BitLocker isn't available, another piece of software should encrypt the data, for instance the free-to-own open source program Truecrypt. Another alternative would be the use of a hard drive or SSD that independently encrypts all of the data it stores. These drives carry the acronym SED, which stands for "Self-Encrypting Device". The encryption occurs in real-time during the transfer of data. Access to the data is either dependent on a hardware constellation (for example a TPM chip or BIOS) or on a piece of software that uses passwords to control access.
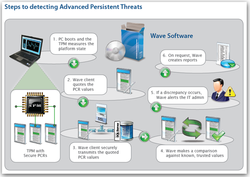
A TPM chip can also be used as protection against virus software and other hacker tools. Big advantage: The protection begins when the device is turned on, even before the operating system boots. One example of this is the Wave Endpoint Monitor, which is specially designed for business customers.
TPM protection doesn't need to replace the use of a Smartcard or fingerprint scanner -- it can also supplement them to make the device even more secure.
Anti-Theft
In addition to the mentioned options designed to limit access, there are also mechanisms of protection that activate when a notebook is lost or stolen. Such solutions exist under the bracket term "anti-theft". They are intended to help locate a lost or stolen notebook and to render data inaccessible to third parties. Solutions exist that are entirely software-based, and there are also options integrated into the motherboard. But they all have this in common: They activate when it's already too late -- that is, when the notebook has already been stolen.
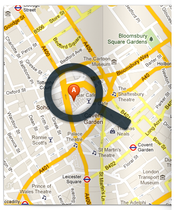
The pure software solutions include programs like Norton Anti-Theft, Snuko Anti-Theft Security and Prey. They can be installed on any notebook. All three locate the whereabouts of a missing notebook either with the assistance of the computer's built-in GPS or by pinpointing the access point through which the notebook makes contact with the Internet. Users can read this information via a web browser. A user can see the location of the notebook on a map and direct the police to that spot. Depending on the solution and the version, it's also possible to take screenshots of the thief, to block access from a distance, and to delete, encrypt, protect or hide data. Often it is also possible to send the thief a direct message on the screen. Such solutions simultaneously permit the user to protect Smartphones through the same means. Norton Anti-Theft charges an annual fee of 40 Euros (~$54) for this service. The protection covers three devices. Snuko charges $30 (~23 Euros) to protect a notebook using their Anti-Theft Security. The open source project Prey is free to use, though it also has a pro-version with extended options and prices starting at $5 a month (~4 Euros).
Hardware Protection
Downside to the anti-theft software solution: They only activate if the thief connects the notebook to the Internet. If he or she switches out the hard drive before accessing the Internet, the notebook can no longer be located and the data is lost. Hardware-based anti-theft solutions like Computrace by Absolute Software and Intel AntiTheft offer options without that flaw. Both require the corresponding hardware and thus can't be used with just any notebook. Computrace protection is integrated into the BIOS, so it remains even if a thief switches out the hard drive before connecting the computer to the Internet. You can find out which notebooks support Computrace here. The software LoJack is needed to activate and control the protection functions. LoJack makes contact with Absolute Software's server once a day. If the notebook is reported stolen, the frequency of contact is increased to four times per hour. The device can be located through the Internet. In case of theft data can be deleted but not encrypted. In order to prevent the thief from seeing the data before the point of localization, this method of protection should be combined with another solution. The Computrace service costs businesses about 38 Euros (~$51) per notebook per year. At 40 Euros (~$54) private users pay a little bit more.
Intel AntiTheft is integrated into the motherboards of second and third-generation Intel Core processors and in all ultrabooks. The AntiTheft function, as with Computrace, only works after it has been activated. That is possible for a fee. For a one-year protection plan you'll pay 15 Euros (~$20), and for a three-year protection plan 50 Euros (~$67) per notebook. Unlike Computrace, Intel AntiTheft encrypts all the data on the notebook and automatically shuts it down when it connects with the Internet -- as soon as the theft has been discovered and Intel's AntiTheft center has been notified, of course. In the end the notebook will no longer start. The screen only displays a customizable message. If the device is returned to its owner, he or she can remove the protection and continue to use the data.
In order to protect the data without the necessity of Internet contact, it's possible to automatically activate Intel AntiTheft when, for example, a certain number of failed login attempts have taken place, or when the notebook hasn't connected to the company server within a certain time frame. These triggers need to be determined prior to a potential theft -- they cannot be changed after a theft has taken place. A password is needed to reactivate the device. This password should be well thought out and very difficult to guess, otherwise the thief could still get to the data. You can find out which notebooks support Intel AntiTheft here.
A difficult-to-guess access code is important for other anti-theft solutions as well -- otherwise hackers can do damage even if they haven't stolen the device. If a hacker were to login to the website of a protection service with the correct access information, depending on the service, he or she could gain full access to the data. The hacker could then look at it and afterwards delete it.
Anti-theft solutions are an ideal and important supplement to access controls. Their advantage: They increase data protection in that they assist in the speedy recovery of stolen notebooks. The stolen device can be easily located and the thief can be arrested. Hardware-based solutions like Computrace by Absolute Software or Intel's AntiTheft function independently from the utilized data storage unit. This of course only works to locate the device once the system has been booted and connected to the Internet, which is a likely scenario if the thief believes to have disposed of any protection that may have resided on the hard drive. But if the thief is knowledgeable regarding the possibilities that various protection systems offer, he or she might avoid network contact. For that reason access to data should be as effectively protected as possible.